
“I never download anything – how could I be at risk?”
Accepting and running a downloaded file is now no longer a necessity: so-called ‘drive by downloads’ have completely changed the way we come into contact with malware.
An era of active content allows us to do incredible things inside our browsers, but the inherent risk now means that even loading a web page or opening an email could be enough to breach your computer’s security.
##Anatomy of a Drive-By Download## A typical drive-by download attack will take place completely undetected by the user, with the simple execution of code on the webpage. This code can take advantage of vulnerabilities or zero days in web-enabled apps you have installed, your browser, or even your operating system.
However, the initial code is often very small and usually has one job: to contact another server from which it can download the rest of the malicious code to your device.
Many websites with malicious code will have several forms of this initial code, in the hopes that one will match your device’s specifications and weak points. For example, there might be code targeting OS X, Windows 7, Android 4.4 and iOS 8 – all within the same page.
Can you tell at a glance whether a site is carrying this malicious code? Unfortunately not.
Drive-by downloads can be placed on specifically-designed malicious sites, but more often they’re found on the sites of many small businesses, schools and individuals, who have no idea their site is infected.
What’s Being Done?##
You might have noticed that when visiting some search engine results, you’re instantly greeted by a security warning screen like the one below:
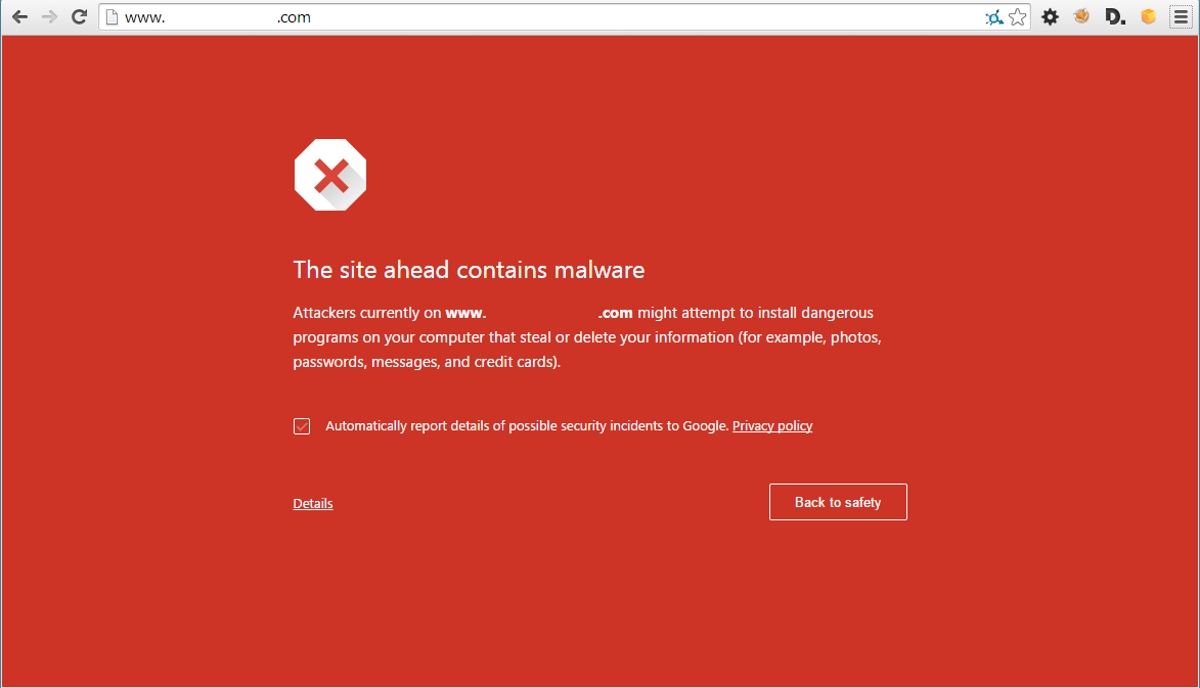
These error messages are served by your browser in response to visiting a site that has made the list of Google or a specialised indexing service (for example, StopBadware) for containing malicious downloads.
Sites in these lists are added by user submissions and special ‘web crawling’ software robots that scan millions of pages for traces of malware. This approach isn’t foolproof, but can help prevent many unsuspecting stumbles into dangerous territory.
The other part of the equation is user behaviour. Learn not to make so-called ‘risky clicks’ – following links to sites you don’t recognise or that don’t feel quite right. These sites might include free streaming of current blockbuster movies or TV shows, adult content, pirated software (“warez”) or stores featuring “too-good-to-be-true” prices – eg. 70 or 80% off retail – for designer goods.
However, if you stumble on the site of a small business or personal blog that triggers your browser’s alert system, do your bit and inform the site’s owner. They may be blissfully unaware that they’ve been compromised, and there are many things they can do to remove the malicious code from their site.
